If you are using custom C# .Net code to connect to SharePoint Online (Microsoft 365) and suddenly start receiving error message "The underlying connection was closed: An unexpected error occurred on a send.", you have reached the right place, lets fix this together.
You may also see a trace with message "Authentication failed because the remote party has closed the transport stream."
This could be a connection failue from Azure App Service to SharePoint, or custom .Net code (Task Schedular / Windows Service / Console) to SharePoint.
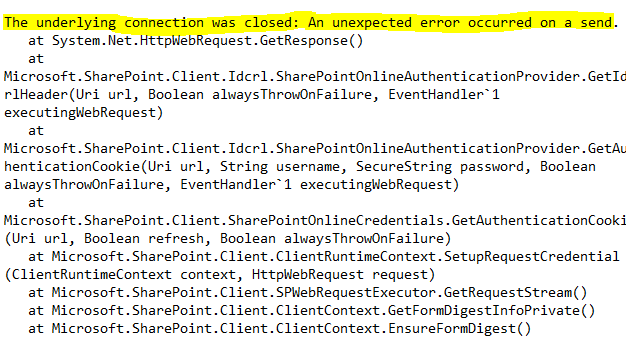
⚠️ Why connection failed at System.Net.HttpWebRequest.GetResponse() ?
Most probably, you may be using TLS 1.0 or 1.1 with .Net Framework 4.0 or 4.5 in your C# code.This is a common problem for legacy applications.
The Transport Layer Security (TLS) 1.0 and 1.1 protocols are deprecated for the Microsoft 365 services. There was temporarily halt due to COVID-19 situation, but TLS 1.2 enforcement is now rolling out.
⭐ What is TLS (Transport Layer Security) ?
Office client relies on Windows web service (WINHTTP) to send and receive traffic over TLS protocols.Transport Layer Security (TLS) secures communication between computers, most commonly with Hypertext Transfer Protocol Secure (HTTPS). Older protocol versions of TLS are less secure than TLS 1.2 and TLS 1.3 and are more likely to have new vulnerabilities.
Older protocols should be avoided to minimize risk and deprecated security protocols should not be used.
By default, .Net Framework 4.5.1 uses TLS 1.0. Does not matter if the platform supports newer TLS protocol versions. Due to this reason, your custom application cannot connect to SharePoint Online and throws connection exception.
⭐ How to enable TLS 1.2 in C# code ?
- Upgrade your application to .NET Framework 4.7.* or newer so it automatically uses TLS 1.2 by default. This is not the easiest approach and may require re-compiling the application.
- Manually force the code to use TLS1.2 protocol (System.Net.Http.HttpClient)
- Manually specify in code to use either of the TLS protocols (preferred approach)
- Update the associated configuration file to use the strongest available cryptography
- Update the associate configuration file to use TLS 1.2 by changing the target framework runtime
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
ServicePointManager.SecurityProtocol = ServicePointManager.SecurityProtocol Or SecurityProtocolType.Tls12 And Not (SecurityProtocolType.Ssl3 Or SecurityProtocolType.Tls Or SecurityProtocolType.Tls11)
ServicePointManager.SecurityProtocol = (SecurityProtocolType)768 | (SecurityProtocolType)3072
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls Or SecurityProtocolType.Ssl3
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<runtime>
<AppContextSwitchOverrides value="Switch.System.Net.DontEnableSystemDefaultTlsVersions=false"/>
</runtime>
</configuration><configuration>
<system.web>
<compilation targetFramework="4.5.1" />
<httpRuntime targetFramework="4.7.2"/>
</system.web>
</configuration>⚡️ .NET frameworks and TLS support
- .NET 4.6 and above - Supports TLS 1.2 by default. Upgrade code to this version if possible, this is a long term solution.
works well, no changes neededServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12ServicePointManager.SecurityProtocol = (SecurityProtocolType)3072;no workaround, only upgrade is a solutionHave Questions? Post them here!
- SharePoint error - An exception occurred when trying to issue security token: This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms..
- PowerShell iterate and get all SharePoint sites and sub sites
- SharePoint Online: Editing session has ended Message
- How to Share Microsoft SharePoint Site with Users or Groups
- How to delete SharePoint Online List Item using REST API
- SharePoint List excel import - This table exceeds the maximum number of supported rows
- How to disable SharePoint subsite creation option for owners
- SharePoint 2010 August 2015 Update KB3055049 - Duplicate Document ID issue bug fixed
- SharePoint Server 2016 Preview installation error - This Product Key isn't a valid Microsoft Office 2016 Product Key. Check that you've entered it correctly.
- How to upload file programmatically to SharePoint Document Library using Server Object Model C# .Net
- Access URL for SharePoint Tenant Admin Center (Online Office 365)
- Error when deleting SharePoint Online folder or file
- How to extend retiring SharePoint 2010 Workflows and continue with Office 365
- How to generate client id and secret to register SharePoint App with OAuth
- How to delete SharePoint List Item programmatically using C#.Net
- How to retrieve all SharePoint Online List Items using Rest API
- [Solved] SharePoint Search Internal server error exception
- Create SharePoint Site Collection using PowerShell New-SPSite
- Fix SharePoint PowerShell error - The term Get-SPweb is not recognized as the name of a cmdlet function script file or operable program
- How to enable anonymous public access for SharePoint Online site collection, file, folder without login ?
- SharePoint Server 2016 installation System Hardware requirements
- How to create SharePoint Online List Item using REST API
- Changed AD user display name showing old name in SharePoint
- Recommended size and resolution for SharePoint Online Site logo
- Microsoft 365: How to Turn Off Delve in SharePoint Online for All Users
- Android Emulator cannot be opened because the developer cannot be verified. [M1 Mac] - Android
- Screen Mirroring iPhone to TV - iOS
- MySQL: How to Select Database via Terminal/Command Line - MySQL
- How to see storage usage details on OneDrive on Mac? - Windows
- How to install pip on macOS using terminal command [Python] - Python
- 3 Ways to Change Default 8080 Port in Spring Boot - Java
- How to Recover Deleted Messages on iPhone - iOS
- How to check your IP using bash for Windows? - Bash