At times when you do not get an error, or do not see the specific information that you are looking for using the cURL command, you can run it in verbose mode.
There are two ways you can run a cURL command in verbose mode.
- -v : short hand option.
- --verbose : long hand option.
curl -v http://code2care.org
* Trying 172.67.164.66:80...
* Connected to code2care.org (172.67.164.66) port 80 (#0)
> GET / HTTP/1.1
> Host: code2care.org
> User-Agent: curl/7.85.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 301 Moved Permanently
< Date: Wed, 30 Nov 2022 06:28:18 GMT
< Transfer-Encoding: chunked
< Connection: keep-alive
< Cache-Control: max-age=3600
< Expires: Wed, 30 Nov 2022 07:28:18 GMT
< Location: https://code2care.org/
< Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=t
yhXfH5HzZ2lNGOwsNHd"}],"group":"cf-nel","max_age":604800}
< NEL: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
< Server: cloudflare
< CF-RAY: 772185adfe4a85b9-BOM
< alt-svc: h3=":443"; ma=86400, h3-29=":443"; ma=86400
<
* Connection #0 to host code2care.org left intactAs you can see, using the -v option or flag, you get more information about the IP address and the Port you are trying to connect to, and using the HTTP 1.1 version. The default User-Agent used here for the GET request is the curl version 7.85.0 and Accept is */*.
In verbose details you can see that the URL has been redirected to a secure HTTPS URL with a 301 redirection.
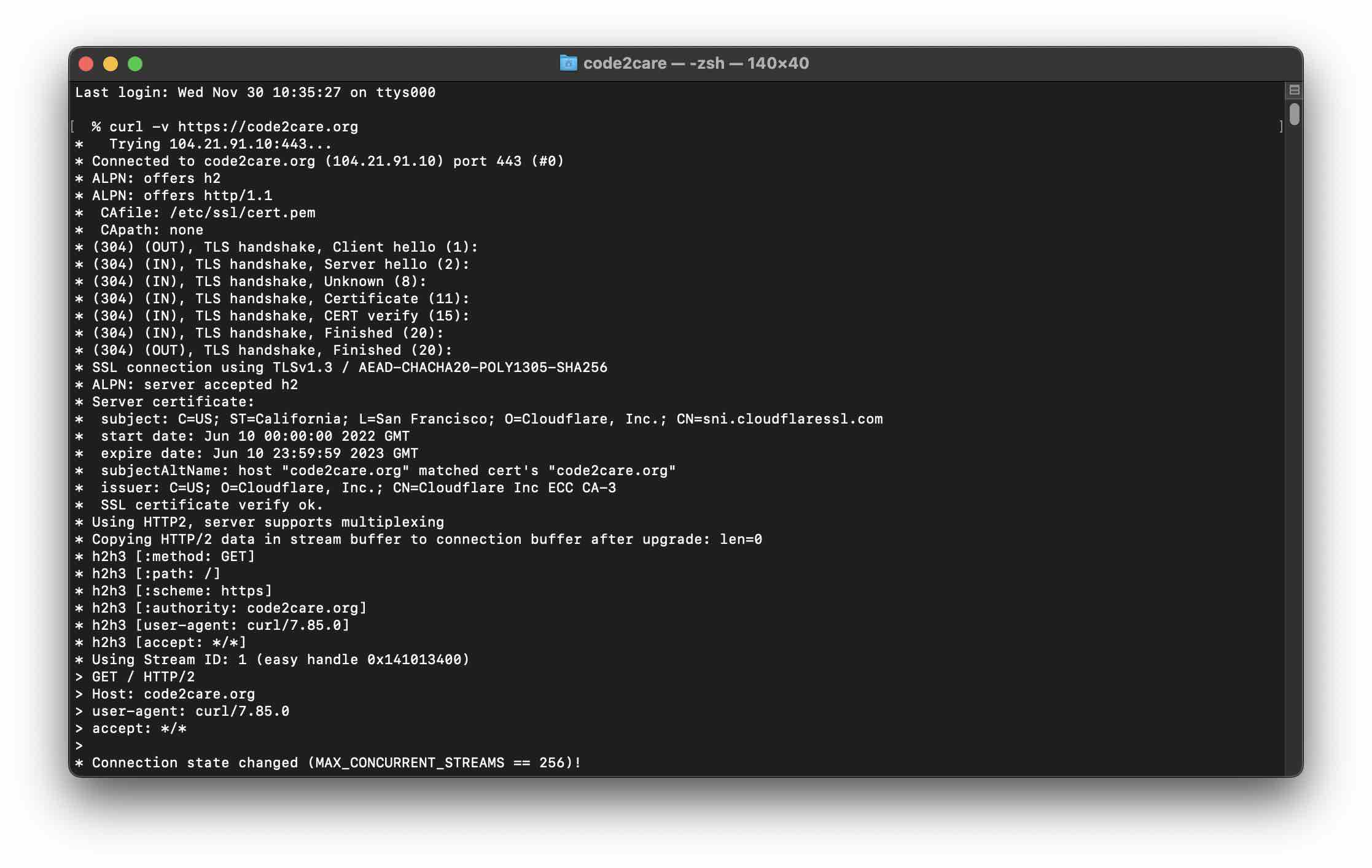
Example 2:% curl --verbose https://code2care.org
* Trying 104.21.91.10:443...
* Connected to code2care.org (104.21.91.10) port 443 (#0)
* ALPN: offers h2
* ALPN: offers http/1.1
* CAfile: /etc/ssl/cert.pem
* CApath: none
* (304) (OUT), TLS handshake, Client hello (1):
* (304) (IN), TLS handshake, Server hello (2):
* (304) (IN), TLS handshake, Unknown (8):
* (304) (IN), TLS handshake, Certificate (11):
* (304) (IN), TLS handshake, CERT verify (15):
* (304) (IN), TLS handshake, Finished (20):
* (304) (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / AEAD-CHACHA20-POLY1305-SHA256
* ALPN: server accepted h2
* Server certificate:
* subject: C=US; ST=California; L=San Francisco; O=Cloudflare, Inc.; CN=sni.cloudflaressl.com
* start date: Jun 10 00:00:00 2022 GMT
* expire date: Jun 10 23:59:59 2023 GMT
* subjectAltName: host "code2care.org" matched cert's "code2care.org"
* issuer: C=US; O=Cloudflare, Inc.; CN=Cloudflare Inc ECC CA-3
* SSL certificate verify ok.
* Using HTTP2, server supports multiplexing
* Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
* h2h3 [:method: GET]
* h2h3 [:path: /]
* h2h3 [:scheme: https]
* h2h3 [:authority: code2care.org]
* h2h3 [user-agent: curl/7.85.0]
* h2h3 [accept: */*]
* Using Stream ID: 1 (easy handle 0x141013400)
> GET / HTTP/2
> Host: code2care.org
> user-agent: curl/7.85.0
> accept: */*
>
* Connection state changed (MAX_CONCURRENT_STREAMS == 256)!
< HTTP/2 200
< date: Wed, 30 Nov 2022 06:47:03 GMT
< content-type: text/html; charset=UTF-8
< cache-control: private, max-age=0, must-revalidate, no-cache, no-store
< content-security-policy: upgrade-insecure-requests;
< display: pub_site_sol
< expires: Tue, 29 Nov 2022 06:47:02 GMT
< pagespeed: off
< response: 200
< set-cookie: ezoadgid_395744=-1; Path=/; Domain=code2care.org; Expires=Wed, 30 Nov 2022 07:17:02 UTC
< set-cookie: ezoref_395744=; Path=/; Domain=code2care.org; Expires=Wed, 30 Nov 2022 08:47:02 UTC
< set-cookie: ezosuibasgeneris-1=75d082ee-ab6e-432a-669a-3b71899c0c9a; Path=/; Domain=code2care.org; Expires=Thu, 30 Nov 2023 06:47:02 UTC; Secure; SameSite=None
...
< set-cookie: lp_395744=https://code2care.org/; Path=/; Domain=code2care.org; Expires=Wed, 30 Nov 2022 07:17:02 UTC
< set-cookie: ezovuuidtime_395744=1669790822; Path=/; Domain=code2care.org; Expires=Fri, 02 Dec 2022 06:47:02 UTC
< set-cookie: ezovuuid_395744=141c0559-522d-4421-5784-29b4ef97d07e; Path=/; Domain=code2care.org; Expires=Wed, 30 Nov 2022 07:17:02 UTC
< vary: Accept-Encoding
< x-content-type-options: nosniff
< x-ez-proxy-out: true 2.3
< x-ezoic-cdn: Bypass
< x-frame-options: SAMEORIGIN
< x-middleton-display: pub_site_sol
< x-middleton-response: 200
< x-origin-cache-control:
< x-sol: pub_site
< x-sucuri-cache: HIT
< x-sucuri-id: 15037
< x-xss-protection: 1; mode=block
< cf-cache-status: DYNAMIC
< report-to: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?
s=..%2BUBT%2B7P%%2BS%2FSElLkW%2F"}],"group":"cf-nel","max_age":604800}
< nel: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
< server: cloudflare
< cf-ray: 7721a1201895f2aa-BOM
< alt-svc: h3=":443"; ma=86400, h3-29=":443"; ma=86400
<
<!DOCTYPE HTML>....<HTML>
* Connection #0 to host code2care.org left intactIn the above example, we tried to connect to the HTTPS version of the homepage, and you now see a whole, not of more information which includes connecting to the 443 port and the details about the TLS 1.3 certificate and CA Cert details and the TLS handshake details and HTTP/2 GET response with status 200 and a list of Response headers and cookie details.
After all the details you get the HTML payload which I have trimmed to make it more readable.
Facing issues? Have Questions? Post them here! I am happy to answer!
Rakesh (He/Him) has over 14+ years of experience in Web and Application development. He is the author of insightful How-To articles for Code2care.
Follow him on: X
You can also reach out to him via e-mail: rakesh@code2care.org
- cURL Option to show HTTP Response Status Code
- URL Encode cURL HTTP GET\POST Data with Examples
- Capture cURL Request Output to a File
- Fix: Curl No Match Found Error
- trurl: A new command-line tool for URL parsing and manipulation by cURL Developer
- Send JSON Data as Payload using cURL HTTP POST Request
- cURL: Show Request and Response Headers
- Get cURL command from Chrome Inspect Network HTTP URL
- Save cURL Command Output to a external file
- cURL DELETE Request with Examples
- How to URL Encode Data for a cURL Request Parameters
- cURL Example using IP (IPv4 and IPv6) address and Port
- How to convert a Postman request to cURL Command
- [fix] command not found curl
- How to Pretty Print cURL JSON Output in Terminal
- How to follow redirects in cURL Command Request
- How to pass authorization header using cURL
- cURL -x Use of HTTP Proxy Server Examples
- Downloading Google Chrome using cURL Command
- How to get cURL Command to run in verbose mode?
- List of 28 Protocols supported by cURL with Examples
- Hide cURL Outputs and Errors on Terminal
- cURL -d Option with Examples
- How to show SSL Certificate details using cURL Command
- Perform Basic Authentication using cURL with Examples
- How to fix Jenkins Plugin Stuck in Uninstallation pending Status - Linux
- Python: Merge DataFrames Pandas Outer Join Example - Python
- Cannot load PowerApps form in SharePoint Online due to repeated authentication - SharePoint
- Add scroll to div element in HTML Css - CSS
- Fix: Jupyter Notebook Black Web Page on Localhost - Python
- How to Change Bootstrap Carousel Slide Speed - Bootstrap
- How to create StackOverflow error in java - Java
- Efficient way to perform HTTP cURL GET/POST Requests with Payload - cURL